Simulate real-world attacks to uncover and address security weaknesses, ensuring your systems are resilient against cyber threats.
"With years of industry experience, Gcssystems Limited brings expert knowledge and cutting-edge tools to conduct thorough penetration testing. We help businesses uncover hidden security risks."
"Our certified ethical hackers follow industry best practices to provide real-world attack simulations that help prevent breaches before they happen."
"Each penetration test is tailored to your unique infrastructure, ensuring you get the most relevant insights into your security posture."
"We don’t just find vulnerabilities – we provide actionable recommendations to mitigate them, enhancing your network’s resilience."
"Gcssystems Limited has successfully helped businesses in various sectors, including finance, healthcare, and e-commerce, secure their digital environments."

We offer a range of penetration testing services to meet the needs of different industries and infrastructures.
Identify vulnerabilities in your network architecture, routers, and firewalls. We simulate advanced attacks to find exploitable weaknesses and fix them before malicious actors do.
We conduct thorough assessments of your web applications, identifying common vulnerabilities like SQL injection, XSS, and other threats that could compromise your data integrity.
Our experts assess the security of your mobile apps, testing them for potential vulnerabilities in iOS and Android platforms, ensuring your apps are safe for users.
Ensure your Wi-Fi network and communications are secure from unauthorized access and attacks like brute-force and man-in-the-middle.
We simulate phishing, pretexting, and other social engineering attacks to see how vulnerable your employees are to psychological manipulation.
As businesses increasingly move to the cloud, we help assess cloud infrastructure security to prevent unauthorized access to sensitive data stored online.
addressing security vulnerabilities. Through comprehensive assessments, we simulate real-world cyber threats to evaluate system defenses, uncover weaknesses, and provide actionable recommendations. Our goal is to enhance your organization’s security posture by proactively mitigating risks before they can be exploited.
We begin by understanding your security needs and current network infrastructure.
We tailor the test to your environment, selecting the right approach and tools for your business.
Our certified professionals simulate realistic attacks to identify vulnerabilities across your systems.
After completing the test, we deliver a detailed report that outlines vulnerabilities, severity levels, and actionable recommendations.
We assist in fixing the identified issues and provide re-testing services to verify that the fixes are effective.
Penetration testing provides an in-depth assessment of your security posture by mimicking a real-world cyber attack. It helps uncover weaknesses and prevent costly data breaches.
Testing helps you understand how your security systems respond to threats and fine-tune your incident response plan for faster reaction during an attack.
Our network penetration testing services help identify and exploit weaknesses in your network’s architecture, firewalls, routers, and protocols. We simulate sophisticated external and internal attack scenarios to assess your network’s ability to resist unauthorized access and attacks.
After gaining access, we evaluate the extent to which an attacker can move across your network, escalate privileges, and gain deeper access.
Key Benefits: Identify exposed network ports, secure critical assets, and avoid breaches.
Our ethical hackers conduct thorough assessments of your web applications, focusing on common vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure data storage.
Key Benefits: Secure your user data, maintain business continuity, and protect your brand’s reputation.
We assess mobile applications on both iOS and Android platforms to identify vulnerabilities, insecure data storage, and weaknesses in API integrations.
Key Benefits: Ensure user data privacy, prevent app-based attacks, and protect your mobile ecosystem.
As businesses migrate to cloud environments, securing cloud infrastructure is crucial. Our cloud security testing evaluates the architecture, access controls, and compliance of your cloud services.
Key Benefits: Protect sensitive cloud-stored data, ensure compliance with industry regulations, and mitigate cloud-specific risks.
We simulate social engineering attacks, including phishing and spear-phishing campaigns, to assess employee susceptibility to manipulation and trickery.
Key Benefits: Strengthen employee awareness, reduce human error vulnerabilities, and improve overall security training.
Our team consists of certified ethical hackers with industry-standard qualifications such as CEH (Certified Ethical Hacker), CISSP (Certified Information Systems Security Professional), and OSCP (Offensive Security Certified Professional).
We understand that every organization is unique. Our penetration testing services are customized to fit your specific infrastructure, ensuring the most relevant and useful security insights.
After the test, we provide a detailed report that outlines vulnerabilities, their severity, and the recommended steps to mitigate risks. Our reports are designed for both technical and non-technical stakeholders.
After the test, we provide a detailed report that outlines vulnerabilities, their severity, and the recommended steps to mitigate risks. Our reports are designed for both technical and non-technical stakeholders.
We simulate the tactics, techniques, and procedures (TTPs) of real-world hackers, helping you identify vulnerabilities before attackers can exploit them.
We don’t just stop at the test. Gcssystems Limited offers continuous support to assist with remediation and re-testing to verify vulnerabilities have been addressed.
At Gcssystems Limited, we provide more than just a test. We deliver actionable insights that will help you secure your systems and protect your business from the most advanced cyber threats.
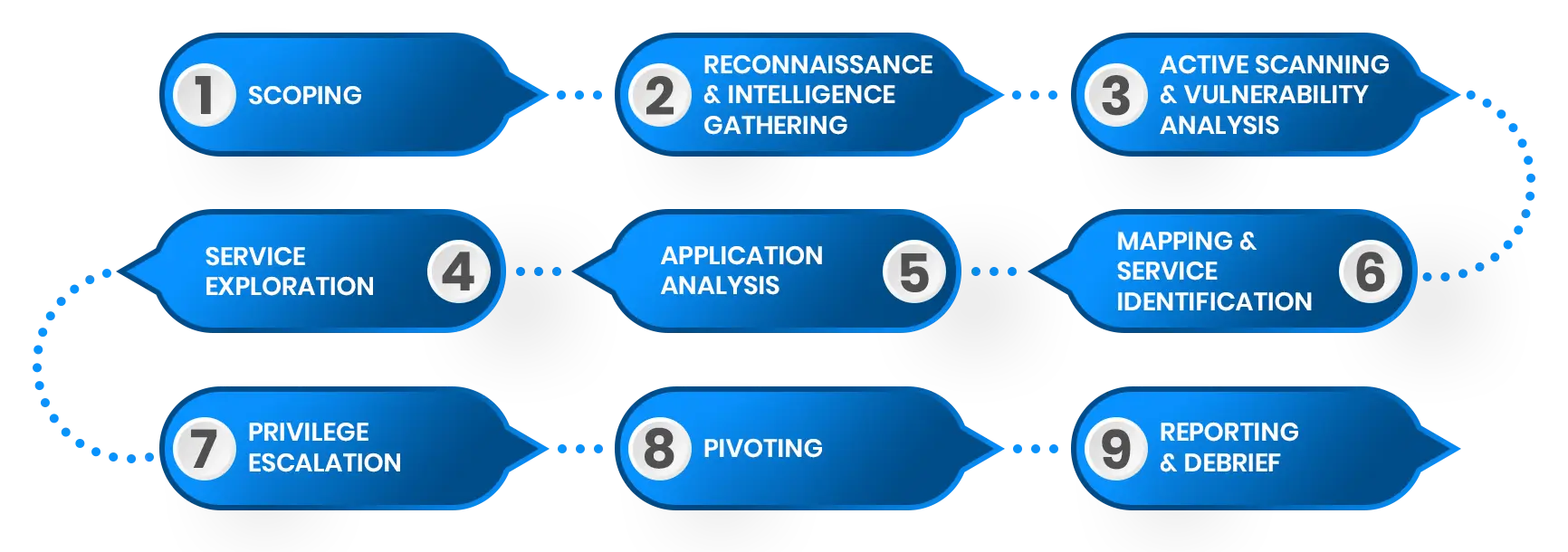
Our penetration testing process is systematic and thorough, designed to uncover vulnerabilities and provide actionable steps for improving your security posture. Here’s how we do it
We collaborate with your team to understand your business goals, infrastructure, and scope of the test. This ensures that the penetration test is focused and aligned with your security needs.”
Our team performs passive and active reconnaissance to collect as much information about your network and systems as possible. We gather details from publicly available sources to build a comprehensive attack surface map.”
We use both manual and automated tools to identify vulnerabilities within your environment. Then, we attempt to exploit these weaknesses to assess the potential impact of a real-world attack.”
After gaining access to your systems, we analyze how deep an attacker can go. We assess lateral movement, privilege escalation, and data exfiltration to determine the full scope of a security breach.”
We provide a detailed report that includes findings, risk ratings, and prioritized remediation steps. Our experts also guide you through fixing the vulnerabilities and offer re-testing to ensure full mitigation.”
defense mechanisms can withstand sophisticated cyber-attacks. Here’s why penetration testing is essential for your business:

Cyber threats are evolving, and proactive testing helps you find and fix vulnerabilities before malicious actors can exploit them.
Many industries require regular security assessments to remain compliant with regulations like GDPR, HIPAA, and PCI DSS. Penetration testing helps meet these regulatory requirements."
Penetration tests assess your organization’s readiness for an attack, helping improve response times and reduce the impact of real incidents.
Penetration testing helps demonstrate to your customers that you take their data security seriously, which strengthens their trust in your services.
Connect with our experts today to explore tailored security solutions for your business. Let us help you safeguard your organization with services designed to meet your unique needs.
Drop your email, and we’ll let you know when we’re ready to show you more.